When it comes to selecting the right software deployment model (or method), while researching or sourcing for B2B tooling, software vendors frequently encounter these terms in the pricing sections – SaaS, BYOC, On-Premises. As deployment environments are getting complicated by the day software vendors need to have a clear understanding of these terminologies and when they should be used. This blog draws a clear comparison and outlines the use cases of each software deployment model. But before that let’s get a clarity between software deployment model and deployment target environment.
Differences Between Software Deployment Model and Deployment Target Environment
Deployment model or method refers to the process of deploying a software. This involves specific techniques and approaches to select a method. Methods are selected based on the level of responsibility sharing for infrastructure management and ownership. Other factors like compliance, security concerns, and customer preferences influence the choice of deployment method.
Deployment target environment is the intended physical environment where vendor-supplied software will run. The driving factor in the selection of a deployment environment is infrastructure characteristics rather than shared responsibilities between vendor and customer. This includes the infrastructure, operating systems, and configurations that support the application.
Key Deployment Models
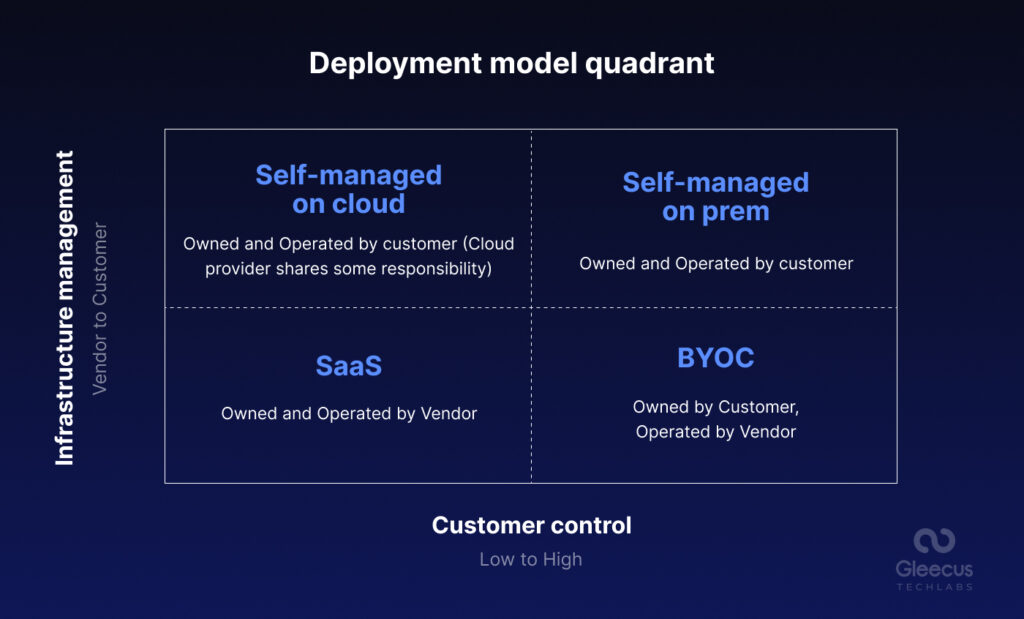
There are three major deployment models.
Fully managed (Cloud) or Software as a Service (SaaS)
All operational and security responsibilities are transferred to vendor. The vendor in turn owns and manages both the software and the infrastructure it runs on. Customer only pays a minimal subscription fee. SaaS is a great solution where ease of use and flexibility prioritizes over data sovereignty. SaaS appeals to customers seeking quick, hassle-free software access without dedicating time or resources to ongoing maintenance.
Bring your own Cloud (BYOC)
The BYOC model grants vendor access to a VPC within the customer’s environment. The data never leaves a VPC environment with the vendor only having restricted access and workload specific permissions to manage the software and infrastructure. A BYOC model is often complemented with a zero-trust security model. The software customer is entitled to discontinue with the vendor at any time. A mature BYOC offers the following:
- Fine-grained Access Controls: Permissions are set at granular level on the ability to access or modify data within BYOC environment.
- Monitoring and Logging: Robust monitoring and logging are performed to track usage, performance, and potential security incidents.
- Clear Service Level Agreements (SLAs): Clearly defined SLAs outline uptime guarantees, supports response times, and issues resolution processes.
- Dedicated Support: Access to knowledgeable and responsive technical support.
Target enterprises and industries of BYOC are large enterprises and organizations operating in highly regulated industries, such as finance, healthcare, and government sectors. They may not have a highly sophisticated infrastructure management team internally. These enterprises strict compliance and data sovereignty requirements barring them from enjoying the benefits of traditional SaaS. BYOC enables them to seek the convenience and expertise of vendor-managed solutions within their own infrastructure.
There is another category of BYOC adopters They are the ones who have invested at bulk on cloud resources like reserved instances or cloud storage at a discounted rate. BYOC enables them to leverage the expertise of vendors and optimize the return of their investments.
On-Premises
On-Premises setups needn’t be confused with the deployment target environment. An on-premises setup could be running in a private cloud environment and not necessarily in an on-premises data center. They offer complete autonomy to organizations. Customers are completely responsible for compliance, security, or operational efficiency. The vendor just issues a license on its behalf and the customer is responsible for infrastructure and software maintenance or maximizing returns on purchased reserved compute or cloud resources. On-premise models are the solution for enterprises requiring complete control over their software and infrastructure. These organizations deploy their internal teams and resources to keep their environment fully private, whether in the cloud or on-premises.
Still having doubts on the right deployment model for your software? Reach out to us.
Factors Driving Choice of Deployment Model
Picking the deployment model happens with a trade-off between control and operational burden. The following are the three major factors influencing it:
Cost
SaaS is the most cost-effective solution for businesses looking for minimal maintenance and predictable costs. For a subscription fee it bundles infrastructure, security, and updates. If your organization has already invested in cloud resources, BYOC can allow you to maximize discount from the reserved instances while sharing management with the vendor. On-premises apparently comes with a premium cost as the customer needs to pay for a dedicated infrastructure and ongoing maintenance. However, the power to enforce strict control requirements and wholesomely manage internal setup can create savings opportunities for companies.
Security
When it comes to security on-premises is the first choice. They offer highest level of security completely restraining external vendors into their environment and also preventing permeation of data outside the environment. But managing all access internally requires extreme expertise in cybersecurity. Lack of experience in configuring private cloud security can lead to failures arising from lack of multi-factor authentication, irregular monitoring, abuse of private cloud APIs, lack of cloud-compliant backup and such . This leads us to find a middle ground in BYOC where control and authority is maintained to an extend but expert cybersecurity team is also roped in. BYOC allows customers to enforce data sovereignty and at the same time lets the vendor handle the software and levels of infrastructure management. SaaS is secure as it is completely the ownership of the provider, but data ownership on behalf of the customer is compromised.
Shared Responsibility
SaaS provider takes complete responsibility while the customer enjoys the product. BYOC follows a shared responsibility model allowing the data to stay in the customers domain while the vendor manages the software and parts of the infrastructure within those boundaries. On-premise on the other hand allows complete control at the cost of substantial internal resource. The customer is completely responsible with security, compliance, performance, and every other factor governing the ROI.
Conclusion
Customers choose to consume software and the environment where it runs based on several distinct factors. A vendor should offer deployment models based on the evolving needs of the customer. Software vendors lacking expertise in robust deployment models beyond SaaS, must unhesitatingly partner with third-parties to ensure they can respond to varied customer needs and enhance their goodwill.
