In today’s digital age, businesses, organizations, and governments of all sizes have integrated computerized systems to enhance daily operations. As a result, ensuring robust cybersecurity has become essential to safeguard data from numerous online threats and unauthorized intrusions.
As we step into a new digital era, the field of cybersecurity stands at the threshold of transformative changes. Cyber threats are not only increasing in frequency but also growing in sophistication, challenging traditional security measures. In this fast-evolving digital landscape, understanding the upcoming trends is crucial for both foresight and preparedness.
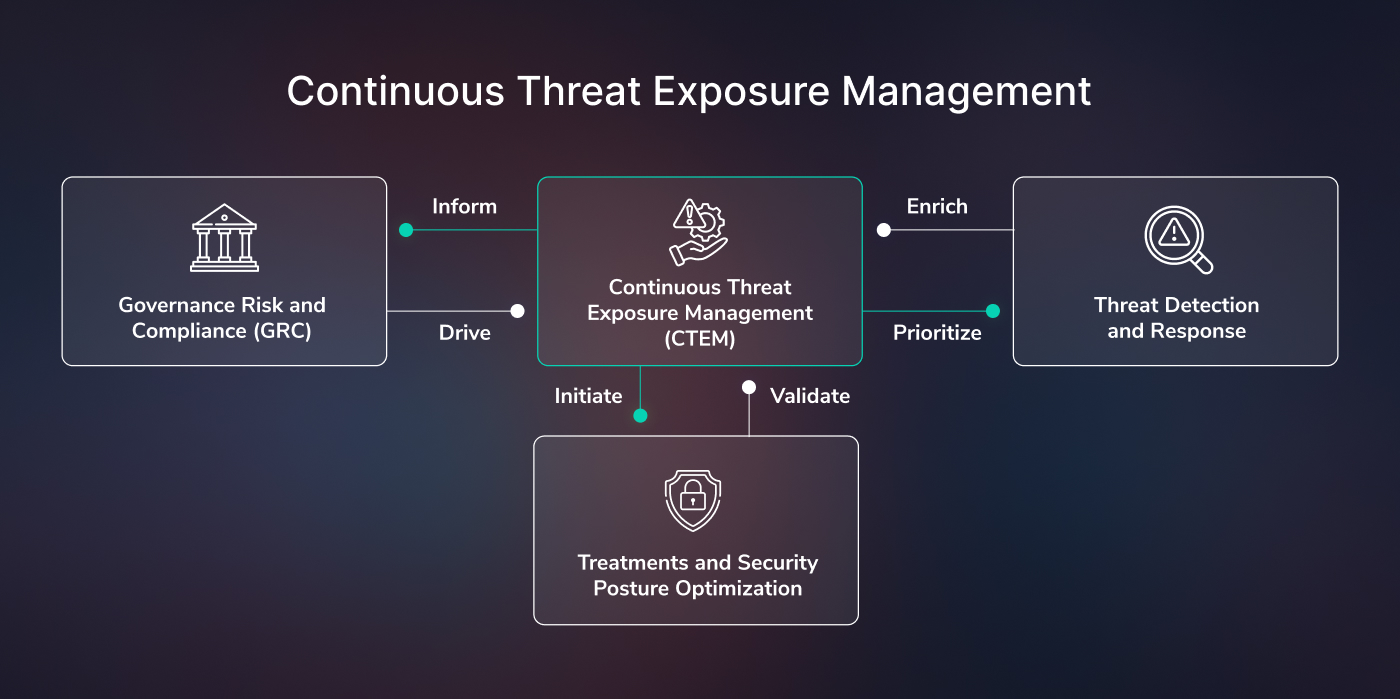
Continuous Threat Exposure Management (CTEM)
Organizations face expanding and diversifying attack surfaces with increased adoption of cloud, social media, and digital supply chains. This broadening landscape makes it difficult for the cybersecurity team to identify and track all security vulnerabilities, resulting in an uncoverable layer of exposure.
Gartner introduced the term CTEM (continuous threat exposure management), a five-stage approach that continuously simulates attacks on an organization’s networks, systems, and assets. By regularly exposing vulnerabilities before real attackers can exploit them, CTEM shifts from reactive to proactive security measures. This ongoing process helps organizations prioritize risk mitigation and refine their security posture, significantly reducing the likelihood of breaches. CTEM continuously refines security posture of your organization by repetitively exposing your organizational assets to stimulated attacks and fix vulnerabilities even before they are discovered by attackers.
IAM
Hackers frequently target compromised user credentials to infiltrate organizational networks through methods like malware, phishing, and ransomware. Protecting these credentials is crucial for businesses. Many organizations are increasingly adopting Identity and Access Management (IAM) technology to secure their data and personnel.
IAM is a comprehensive framework consisting of policies, processes, and technologies designed to manage digital identities and control user access to critical corporate information. By assigning specific roles and appropriate access levels, IAM enhances security, user experience, and business outcomes. It also supports mobile and remote work and facilitates cloud adoption.
The primary goal of an IAM platform is to assign a unique digital identity to each user or device. It then manages, modifies, and monitors their access levels and privileges throughout the lifecycle of the user’s access.
Generative AI for Cybersecurity
In the high-stakes realm of enterprise cybersecurity, staying ahead of constantly evolving threats is a perpetual challenge. For leaders responsible for protecting digital assets, data, and systems, the demand for innovative solutions has never been more critical.
Generative AI is revolutionizing cybersecurity by enhancing professionals’ ability to predict, detect, and respond to threats. Utilizing deep learning models, particularly generative adversarial networks (GANs), this technology simulates advanced attack scenarios, crucial for testing and strengthening security defenses. This rapid adaptation capability ensures robust protection against both known and emerging threats.
Additionally, generative AI automates routine security tasks, freeing cybersecurity teams to tackle more complex issues. It plays a crucial role in training, providing realistic scenarios that enhance IT security professionals’ decision-making skills.
By analyzing patterns in digital communications, such as emails, generative AI can detect subtle signs of phishing that might otherwise be missed, keeping individuals and organizations ahead of cybercriminals.
Generative AI also creates synthetic data resembling real datasets, preserving privacy while training security models. This allows organizations to leverage machine learning benefits without risking exposure of sensitive information, thus safeguarding data privacy and preventing security breaches.
Evolution of Phishing Attack
Phishing attacks have expanded beyond email to include SMS, WhatsApp, and collaboration tools like Microsoft Teams, Slack, and Zoom. This evolution in cyberthreats necessitates a comprehensive cybersecurity strategy addressing the diverse nature of modern communication. Following are some new channels apart from email that are prone to phishing attack:
SMS (Smishing)
Attackers send deceptive SMS messages, often impersonating executives or help desks, to collect personal information. This approach exploits trust instead of sharing some URL which may make the victim suspicious.
Mobile Messaging Apps
Platforms like WhatsApp, Signal, and Telegram are targeted for credential theft or malware installation via phishing messages.
Collaboration Tools
With remote work on the rise, tools such as Microsoft Teams, Slack, and Zoom are exploited by attackers sending phishing links or malicious attachments in chat messages or meetings.
Advancements are enhancing filters to block phishing emails and evolving browser security to detect malicious websites instantly. However, phishing will remain a persistent challenge for organizations in the foreseeable future. Organizations can strategically manage this risk by:
Deploying Anti-Phishing Pen Tests
Conduct social engineering tests to identify employee vulnerabilities and types of phishing that may deceive them. These tests simulate real attacks to pinpoint weaknesses.
Educating Employees
Train employees to recognize phishing signs, such as unusual URLs and unsolicited attachments, and follow best practices, like avoiding links and using resources like OpenPhish and PhishTank.
Regular Retesting
Frequent testing ensures ongoing employee vigilance and helps address new phishing tactics and new employee vulnerabilities.
Zero Trust Security
Zero Trust is a framework designed to secure infrastructure and data amidst today’s digital transformation. It tackles contemporary business challenges such as securing remote workers, managing hybrid cloud environments, and mitigating ransomware threats. While numerous vendors have formulated their interpretations of Zero Trust, aligning with established standards from recognized organizations can assist in integrating Zero Trust principles effectively within your organization.
One reliable standard is the NIST 800-207 standard for Zero Trust, recognized as the most vendor-neutral and comprehensive guideline, applicable not only to government entities but to all organizations. It incorporates elements from other frameworks such as Forrester’s ZTX and Gartner’s CARTA, ensuring compatibility and safeguarding against modern cyber threats in enterprises adopting cloud-first and remote work models.
Zero Trust represents a significant shift from traditional network security, which relied on the “trust but verify” approach. Traditionally, organizations automatically trusted users and endpoints within their perimeter, exposing them to risks from malicious insiders and legitimate credentials compromised by attackers. This outdated model became inadequate with migration to the cloud for digital transformation initiatives and the rapid adoption of remote work environments accelerated by the pandemic.
Implementing this framework involves leveraging advanced technologies like risk-based multi-factor authentication, identity protection, next-generation endpoint security, and robust cloud security technology. These technologies verify user or system identities, assess access permissions dynamically, and maintain ongoing system security. Zero Trust also mandates encrypting data, securing email communications, and ensuring the hygiene of assets and endpoints before they access applications.
Rise of BYOD and Mobile Devices
The Bring Your Own Device (BYOD) trend continues unabated, especially with remote work becoming standard practice. Employees increasingly use personal devices for work, offering flexibility and convenience but also introducing security concerns.
In 2024, we anticipate a further surge in BYOD and mobile device usage. To safeguard sensitive corporate data on these devices, organizations must deploy robust mobile device management (MDM) solutions and enforce stringent security policies. Balancing employee productivity with data protection remains a critical challenge.
State Sponsored Cyber Warfare
Cyber warfare extends beyond rogue hackers to include active involvement by nation-states. In 2024, we anticipate a rise in state-sponsored cyberattacks and espionage, which could have profound geopolitical consequences and disrupt critical infrastructure.
To address this trend, countries must bolster their cybersecurity defenses and collaborate on international cybersecurity initiatives. The global cybersecurity landscape is evolving, emphasizing the crucial role of cooperation in mitigating these threats.
Cybersecurity Reskilling
The cybersecurity sector in 2024 is facing a critical challenge: a significant skills gap. As cyber threats grow more sophisticated, the demand for skilled cybersecurity professionals is surging, yet there’s a notable shortage of individuals equipped to combat these evolving threats. This gap poses risks not only to individual organizations but also to global cyber infrastructure.
To address this issue, educational institutions are expanding their cybersecurity curricula, offering specialized degrees and certifications with a focus on practical, hands-on training. These programs aim to prepare students for real-world cybersecurity challenges.
Professional development and continuous learning have also become essential in a cybersecurity career. Organizations and industry bodies provide various training programs, workshops, and seminars to help current professionals stay updated on the latest trends, tools, and techniques. These initiatives often cover specific areas such as network security, threat intelligence, and incident response.
Public-private partnerships in cybersecurity education are gaining traction. Businesses collaborate with educational institutions to develop training programs aligned with industry needs, benefiting students with relevant skills and the industry with a well-prepared workforce.
As we progress towards a digitally connected era, these educational and training initiatives are crucial in narrowing the cybersecurity skills gap, ultimately leading to a more robust and resilient digital ecosystem.
IoT Security
The Internet of Things (IoT) significantly expands the attack surface of cyberspace by introducing numerous interconnected devices vulnerable to exploitation by threat actors. From smart homes and smart hospitals to industrial IoT systems like digital twins, IoT devices pose unique security challenges due to their inherent complexity and diverse ecosystems. As IoT device proliferation continues unchecked, cybersecurity professionals must tackle the task of securing these networks, implementing robust authentication mechanisms, and protecting against potential IoT-based attacks.
Conclusion
The integration of advanced technologies into cybersecurity is a double-edged sword, as adversaries also seek to exploit these innovations for malicious purposes. AI-powered malware, deepfakes for phishing, and IoT-based botnets exemplify how cybercriminals leverage emerging technologies to execute sophisticated cyberattacks. As defenders strive to stay ahead of evolving threats, they must address the ethical and security implications of incorporating advanced technologies into their cybersecurity strategies.
